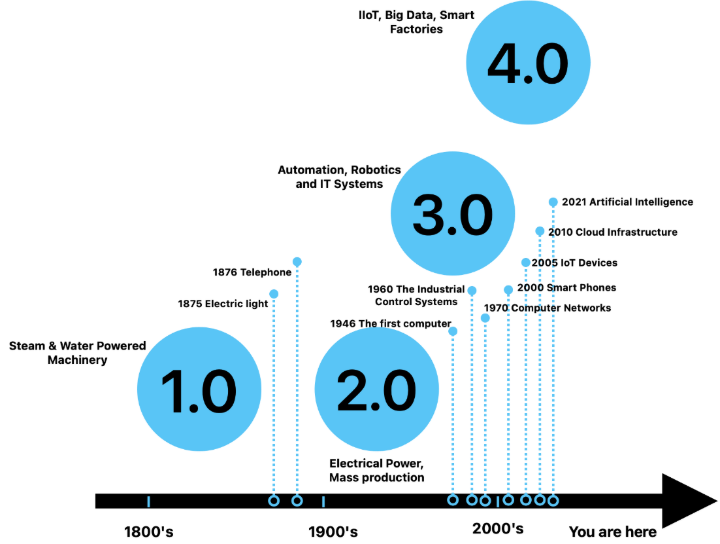
Incident Management for Industrial Control Systems
A practical guide to preparing for, responding to, and recovering from incidents in critical infrastructure environments. Strengthen your incident response strategy & build operational resilience by mastering incident management for …