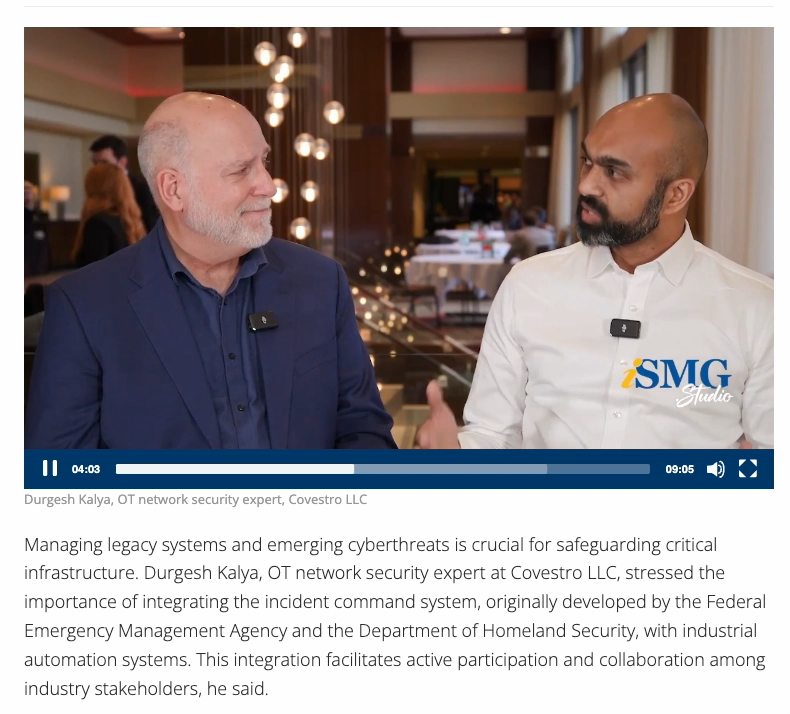
iSMG – govinfosecurity.com on Robust Incident Management for Critical Infrastructure
Ensuring the security of critical infrastructure necessitates managing both legacy systems and emerging cyberthreats. Durgesh Kalya, an OT network security expert at Covestro LLC, emphasized the necessity of integrating the incident command system—initially developed by the Federal Emergency Management Agency and the Department of Homeland Security—with industrial automation systems. This integration promotes active participation and collaboration among industry stakeholders.
“Essentially, everyone is a cybersecurity engineer because they work on computer systems. It’s not possible to update software on hardware that is decades old; modern hardware and equipment are required,” Kalya explained.
In an interview at the Cyber Security for Critical Assets USA Summit, Kalya also addressed the importance of robust incident management frameworks, collaboration between organizations and ICS vendors, and the need for understanding and segmenting systems to mitigate ransomware risks.