IT and OT – Siblings of Modern Critical Infrastructure
When “Smart” Becomes Risky: IT and OT in Modern Infrastructure
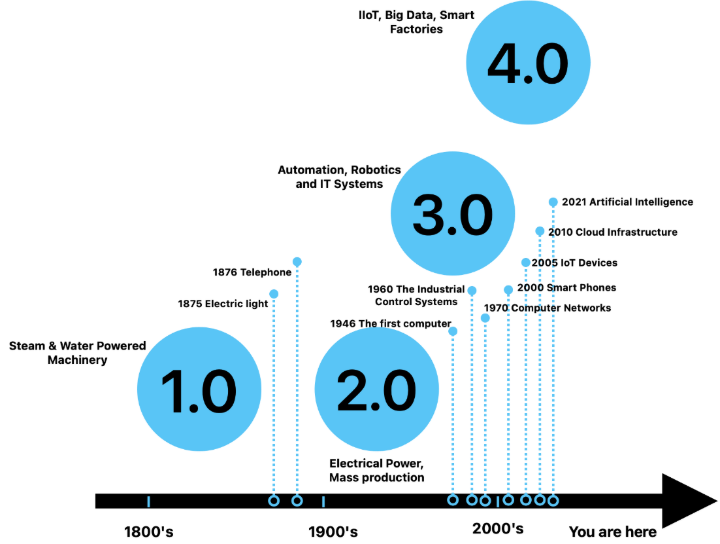
In today’s industrial landscape, Information Technology (IT) and Operational Technology (OT) are no longer distant cousins—they’ve become siblings in the heart of critical infrastructure. As factories, utilities, and supply chains adopt more IoT and IIoT systems, they gain sophistication and efficiency—but also new vulnerabilities. What happens when a sensor fails, a network glitch occurs, or a malicious actor exploits a weakness in a control system? Incident management teams are now bridging the divide between IT and OT—responding to outages, cybersecurity events, and unplanned downtime in environments where the boundaries are blurred.
How do we build trust, clarity, and shared accountability between operations and IT—and ensure that in our pursuit of automation, we don’t accidentally open the gates to systemic risk?